Preventing Costly Data Compromises: 5 Best SAP Mobile Solution Security Practices

Sheriff: “What happened?”
The Stranger: “Somebody left the door open and the wrong dogs came home.”
When you’re the victim of lax mobile device security, you can definitely empathize with the Stranger (Clint Eastwood) from the popular 1973 Western film High Plains Drifter. But the Stranger only lost a few insignificant and easily replaced personal items in this scene. When someone compromises the security of your company’s mobile solution – be it a smartphone, tablet or other smart device - you stand to lose valuable corporate data. You also leave your organization open to additional threats. How can you ensure the door is closed and locked so that the “wrong dogs” don’t get into your system? How can you improve your SAP mobile solutions security and protect your data from someone’s prying eyes, from tampering or other fraudulent action?
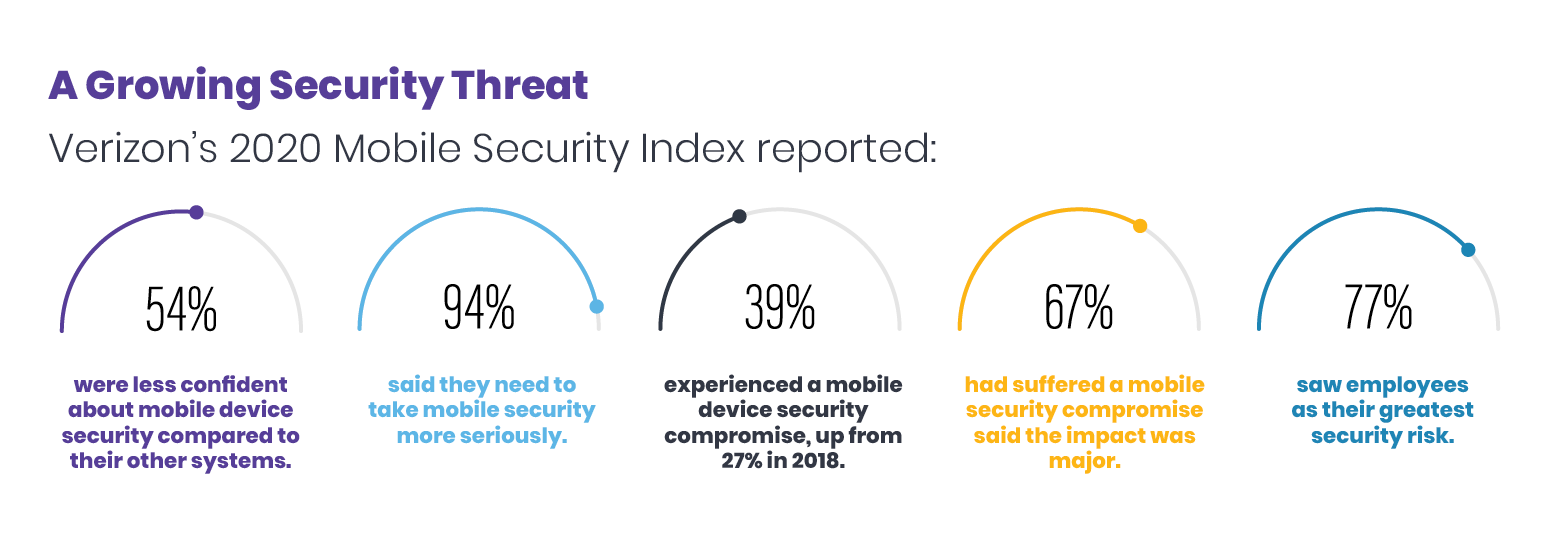
Survey Reveals Serious Mobile Device Security Concerns
Mobile provider Verizon studies mobile device security and threats. The company regularly surveys companies about the issue and puts out a yearly report detailing the results. Those results are often not promising. For example, in 2019 Verizon concluded:
“Many companies are failing to protect their mobile devices. And we’re not talking about some almost-impossible-to-achieve gold standard. We're talking about companies failing to meet even a basic level of preparedness."
In the 2020 survey, 94% of manufacturing companies said they need to take mobile device security more seriously. Two-thirds of respondents admitted they had suffered a security compromise.
Protect Your Data: 5 Best Practices for SAP Mobile Solution Security
You don’t have to be like one of the companies listed in the infographic. There are ways to protect your company and its valuable data while still being able to enjoy the versatility and benefits of an SAP mobile solution. Here are five suggestions and best practices your organization can employ today to increase your SAP mobile solution security.
- Adopt a security-first focus – The first rule of effective security is to trust no one. You and your entire staff, not just IT, must have a security-first mindset. It only takes one electronic door inadvertently left open to compromise your system and your data. The tighter your protection and the greater the vigilance of every employee in your operation, the less vulnerable you’ll be to a breach. Give all employees who use mobile devices regular security training. Keep them constantly informed on potential threats, on how to avoid them and how to report anything suspicious.
- Create an acceptable use policy (AUP) – If your company lacks a codified AUP for bring-your-own mobile device users, you’re placing your organization and your data at grave risk. Rectify that immediately. Write a formal AUP that details user responsibilities, networks they can use and apps they can install. Once the policy is established, don’t just put it in a drawer and forget it. Rigorously enforce it.
- Frequently change passwords – For vendor-issued devices, immediately change all default and vendor-supplied passwords before first use. For bring-your-own devices, mandate frequent password resets and avoid reuse of any previous passwords.
- Employ two-factor authentication – A more effective security suggestion is to eliminate passwords altogether and switch to two-factor authentication. Hacking software has become so sophisticated it is now able to try thousands of stolen passwords simultaneously, rendering such a security measure almost completely ineffective against someone employing such software. Moving to a two-factor authentication system adds an extra layer of security and safety. A two-factor method might employ some combination of username/password, a physical card or electronic security token, or a fingerprint or other biometric trait unique to the user. When two or more of these are used in combination, it makes it much more difficult for an intruder to penetrate a system. The intruder may have acquired a stolen username or password, but without one of the other needed things, entry will be denied, protecting you and your data.
- Implement single sign-on (SSO) – An SSO system works well in complex security situations, like those at an industrial plant. SSOs let a user to log in with a single ID and password to any of several related, yet independent, software systems. This eliminates the need to sign on to each system. An SSO mitigates password fatigue, simplifies username and password management, increases speed and efficiency, cuts down on calls to help desks, and reduces security risks. An SSO can be used in conjunction with two-factor authentication for additional protection.
Learn How a Connected Worker Platform Works Keeps the “Wrong Dogs” from Coming Home to Your System
Innovapptive’s Connected Worker platform takes data security seriously. Our aim is to ease your security fears, not add to them. Each of our mobile solutions utilize SAP data encryption. This protection enables front-line workers to perform their jobs in safety and security without jeopardizing the integrity of your corporate data. Operational data and systems remain sheltered from outside hacking or fraudulent activity designed to do you and organization harm. To discover more, click here to schedule a free demo, or call us at 844-464-6668. One of our experts is standing by to answer any questions about employing a Connected Worker platform and ensuring the safety of your data.

See It In Action
Schedule a personalized demo to see how our solutions can help your business thrive.
- 29-09-2025
Your Ultimate Guide to Connected Worker
In the rapidly evolving industrial landscape, maximizing plant efficiency and ensuring optimal...
- 20-08-2025
Building the future of Industrial Operations with Innovapptive and AWS
Most manufacturers have already gone digital. Yet business outcomes haven’t moved in step. Many...
- 22-04-2025
The $3.6B Unlock: Solving the Chemical Industry’s Labor Crisis and EBITDA Pressure in One Move
“Constraints don’t slow innovation—they force it.”


